SpyPort Serial Sniffer/Logger
Sniffer and Logger for Serial Port
What is SpyPort for SerialTool
SpyPort is a feature of SerialTool that allows monitoring of all serial port traffic, in a Windows environment, directly from the Kernel.
This approach uses a driver specially developed for SerialTool by our team to intercept all calls that the operating system directs to a specific COM port.
More precisely, it is possible to "sniff" the serial communication even if the COM port is open and used by another application because the Kernel Driver intercepts and filters the IRP and IOCTL_SERIAL signals of Windows.
This feature of SerialTool is only available for the PRO version.
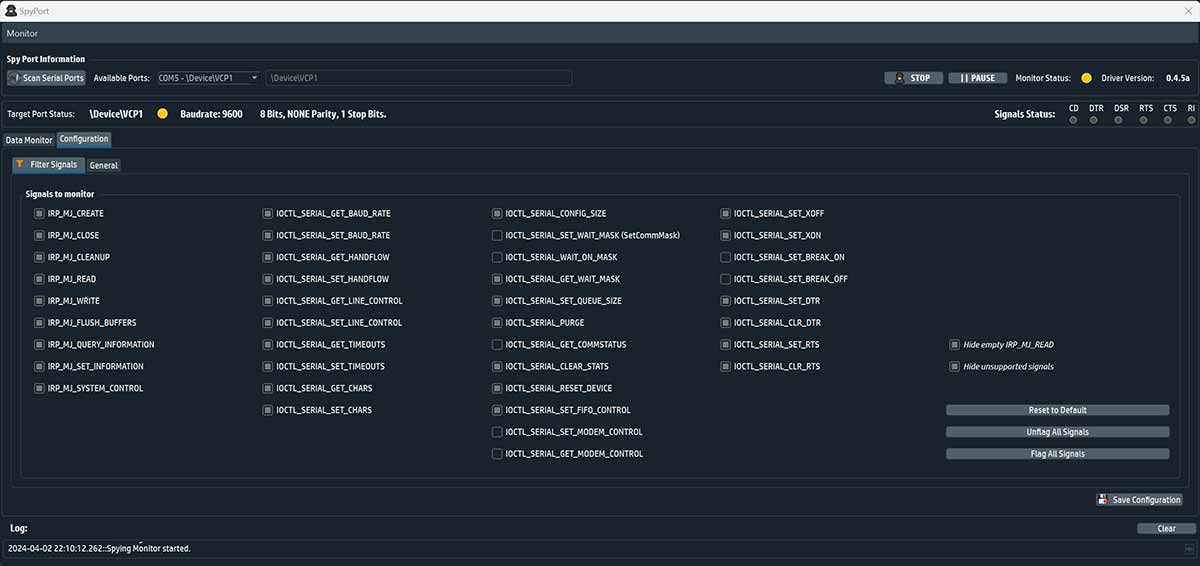
Main Screen
What can be sniffed and logged
It is possible to selectively filter only some of these signals of interest or directly all low-level traffic. SpyPort offers the possibility to save only outgoing traffic (IRP_MJ_WRITE), incoming traffic (IRP_MJ_READ) or all complete traffic by selecting one or all IOCTL_SERIAL. Incoming and outgoing data can be saved in text or binary format for IRP_MJ_WRITE and IRP_MJ_READ (TX and RX of the COM port) and in text format for other signals.
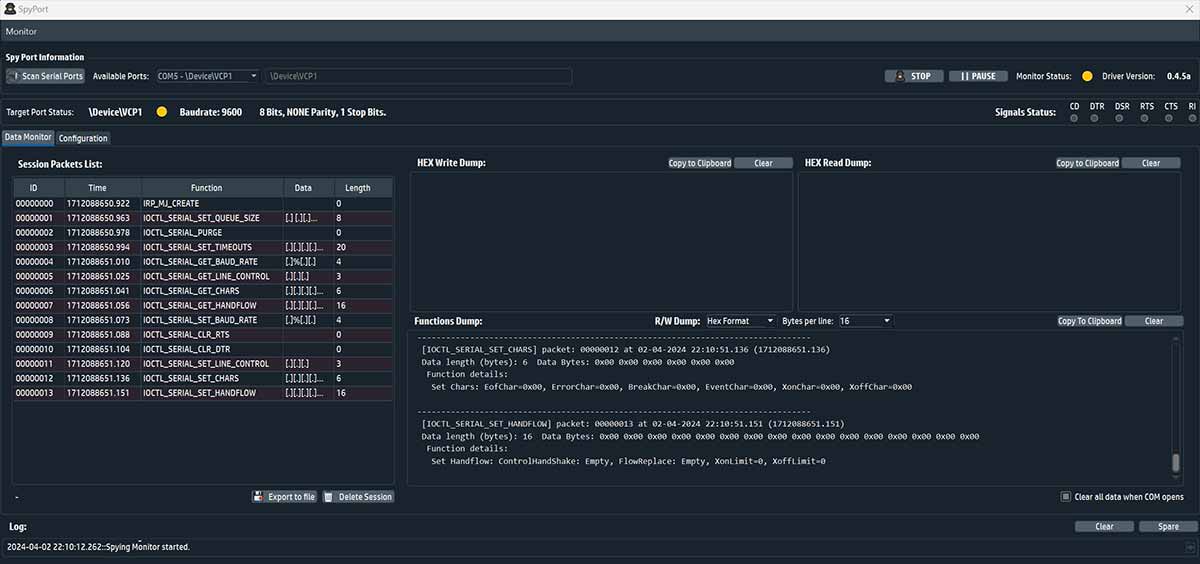
How sniffed/logged data are displayed
SerialTool, thanks to its advanced features, allows viewing each packet in detail, showing the data contained in it in ASCII or Hexadecimal format.
This peculiarity facilitates and promotes a faster and more targeted consultation and at the same time allows to search for specific patterns within a packet or save/export the packet of interest in binary format or copy it to the clipboard in ASCII format.
Each packet is carefully displayed, indicating all the important data such as the precise moment of reception (in milliseconds), the type of packet, the time elapsed between the previous and the next packet.
The packet analysis type follows that of the session packets introduced in version 1.6.0 of SerialTool.
It is possible to stop logging at any time without compromising the software using the COM port at that moment.
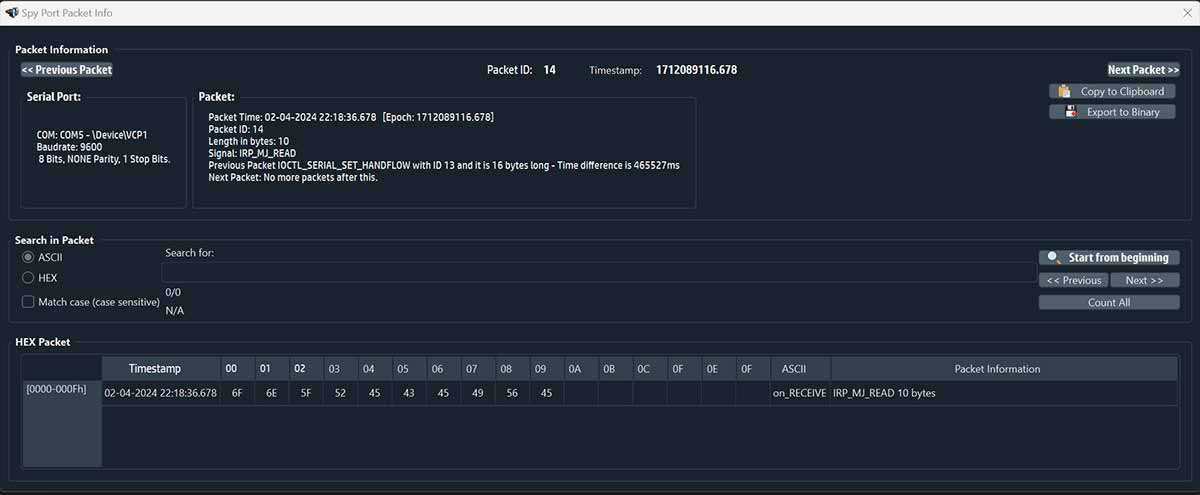
ASCII and Hexadecimal Viewing of a Sniffed Serial Packet.
Examples of using SpyPort with SerialTool
The fields of use of the SpyPort module are multiple, including:
1. Monitoring of own and third-party applications.
In the industrial and embedded world, in the presence of malfunctions, it is very difficult to understand and identify when a bug occurs. Sometimes your own applications or those of third parties have defects that manifest themselves after several hours and the developer cannot be present to intercept the problem and remedy it. For this reason, a SerialTool with its SpyPort module is designed to guarantee long periods of sniffing/logging in an intuitive and effective way, helping the developer to identify the cause of the problem.
A classic example can be an industrial application where the official production software communicates via the serial port with other devices.
If there were to be a defect, it is important to be able to monitor the behavior of the software in its official "release" mode to see where the problem occurs. SpyPort does not interfere with the software under monitoring and allows analyzing all incoming and outgoing traffic.
2. Reverse Engineering.
In a scenario where one wants to "capture" the traffic entering and exiting the serial port of specific software, for example during the download of firmware to a connected device, SpyPort is the ideal tool!
It allows saving directly in binary format all bytes in transmission (COM TX - IRP_MJ_WRITE) of third-party software and capturing the data of interest (e.g. Firmware).
3. Debugging.
When developing software for the serial port, it is absolutely essential to ensure that the data sent and received are correct, follow a certain timing, and sometimes it is also necessary to correctly control other signals of the COM port such as DTR and RTS.
When the developer writes their own software, SpyPort helps to verify that the behavior of the serial port is as expected, that the serial port is opened correctly, and that reading and writing are performed according to the specifications.
In this case, SerialTool with its SpyPort module becomes an essential working tool to check step by step that all the software is written correctly. When intending to create software that communicates with the serial port, SpyPort becomes absolutely indispensable.